A month ago, I experienced the unsettling reality of car theft firsthand when my vehicle was stolen from my driveway in the dead of night. As a cybersecurity journalist with 18 years in the field, I’ve extensively covered car hacking, even interviewing experts like Charlie Miller. Yet, like many, I fell into the trap of feeling detached from the actual threat, thinking “it won’t happen to me.” This experience served as a stark reminder of the pervasive nature of modern car theft and the vulnerabilities, particularly concerning Mercedes Car Keys and keyless entry systems.
While specifying my car as a Mercedes-Benz GLC 220 AMG Line Premium D might seem brand-specific, it’s crucial because the make and model are directly relevant to the theft method. Mercedes-Benz has also contributed to this article, providing valuable insights. Let me assure you, this isn’t about being ostentatious; this was simply the first decent car I’d ever owned.
I’m now among the hundreds of thousands in the UK who face car theft annually. However, my profession allows me a unique opportunity to delve into the expertise of cybersecurity professionals and automotive security specialists to understand exactly how my Mercedes car, and potentially yours, could be silently stolen with a Mercedes car key hack.
The Sobering Statistics of Car Theft
Recent DVLA figures paint a grim picture: a car is stolen in the UK approximately every eight minutes. Office of National Statistics data reveals a staggering 397,264 car thefts in England and Wales between October 2022 and September 2023. This figure, often underestimated in media reports, highlights the extensive scale of the problem.
The most targeted car brand is Land Rover, with Mercedes-Benz unfortunately taking second place, followed by Ford. Recovery rates are discouragingly low, with most sources indicating less than 20% of stolen vehicles are ever recovered.
This reality prompts a critical question: how are these vehicles, especially high-value cars like Mercedes, being stolen without any signs of forced entry, vanishing silently into the night, often due to vulnerabilities associated with the Mercedes car key system?
Was My Mercedes Car Key Hacked?
My Mercedes-Benz GLC 220 AMG Line Premium D was equipped with keyless entry and start, features that, while convenient, also present security risks. The detective investigating my case revealed that six similar vehicles were stolen within a mile radius over just two nights, suggesting an organized crime operation targeting the Oxfordshire area from larger cities like London or Birmingham.
Discovering my driveway empty one rainy morning was a shock. Both Mercedes car keys were exactly where I’d left them inside my house. There was no broken glass or any indication of forced entry on my secluded driveway. The inescapable conclusion was that my Mercedes car had been hacked, specifically, my Mercedes car key system had been exploited.
Cybersecurity expert Graham Cluley, host of the Smashing Security podcast, confirmed my suspicion. “In its broadest sense, hacking is gaining unauthorized access to something, and the criminals who stole your car did just that by exploiting a flaw in its entry system.”
David Rogers, CEO of Copper Horse, a connected car security specialist, agreed: “It’s almost certainly car hacking.” Most experts I consulted concurred.
However, Adam Pilton, a former police officer and detective now a senior cybersecurity consultant at CyberSmart, offered a nuanced perspective. “While ‘car hacking’ might evoke images of sophisticated attacks, the theft of six cars in the area suggests a relay attack, a simpler yet effective method.” This raises an important point: is a relay attack a form of hacking, particularly concerning a Mercedes car key?
Ivan Reedman, director of secure engineering at IOActive, provided a more technical definition. “If we define hacking as gaining unauthorized access to data in a system or computer, this might not strictly be a hack. The criminals gained access to the car, but not necessarily data. I’d argue this is theft facilitated by exploiting a vulnerability, rather than a data-centric hack.”
Relay Attacks: The Mercedes Car Key Vulnerability
Despite differing definitions of “hacking,” the consensus among the eight experts I interviewed was clear: my Mercedes car was stolen using a relay attack, exploiting a vulnerability inherent in my Mercedes car key’s keyless entry system.
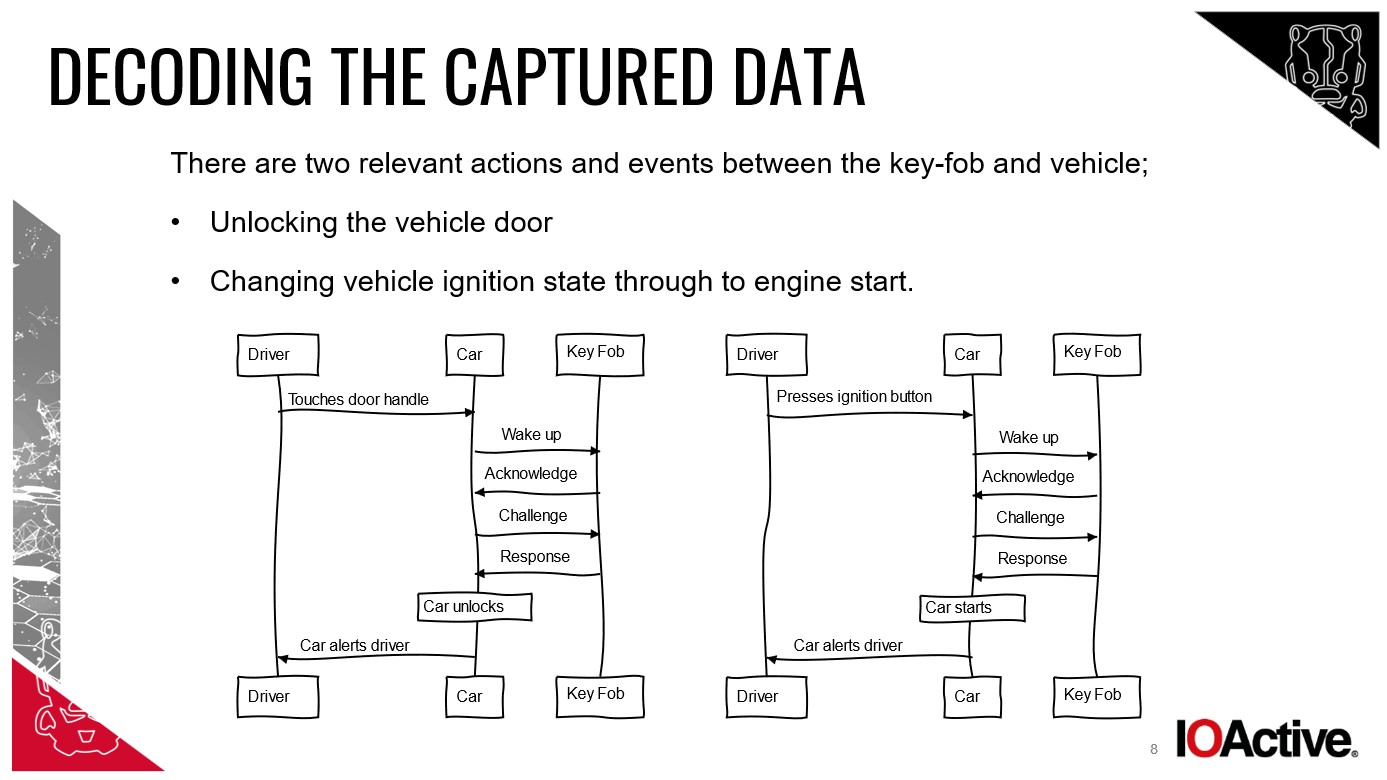
My Mercedes had ‘Passive Entry Passive Start’ (PEPS). This meant with my Mercedes car key on my person, I could unlock and start the car without pressing buttons or even touching the key. This convenience is precisely what relay attacks exploit.
Diagram illustrating the communication between a driver, car, and key fob in normal keyless entry operation.
Chris Pritchard, a principal adversarial engineer at Lares, explained, “Thieves use a tool and aerial to relay the signal between your contactless Mercedes car key and the car. The car is tricked into thinking the key is nearby and unlocks.”
William Wright, CEO at Closed Door Security, elaborated: “They use two devices. One near your house to pick up the Mercedes car key fob signal, even through walls. The other device, positioned by the car, relays that signal.”
Relay devices can operate within 10-15 meters of the Mercedes car key and the attack can take as little as 30 seconds.
Reedman added, “The device relays the fob’s signal to the car, allowing thieves immediate access and enabling them to drive away. It’s a range extension attack, boosting the PEPS range.”
Reedman demonstrated this vulnerability to the BBC using readily available components: an audio amplifier, batteries, and copper wire, unlocking and driving a Mercedes AMG owned by a BBC producer with ease.
Once inside and driving, how did they keep my Mercedes running after the system realized the Mercedes car key was no longer present?
Reedman explained, “Once started, most vehicles alert to the key’s absence but won’t shut off the engine. The engine runs until stopped, at which point thieves can assign a new key and disable yours.”
Cluley emphasized, “Cars won’t suddenly stop if the key signal is lost; that would be dangerous if the key battery died. However, restarting might be impossible without the key.”
Exploiting the On-Board Diagnostics (OBD) Port
Relay attacks get thieves into your Mercedes and started, but to maintain control and potentially reprogram the Mercedes car key system, they need access to the on-board diagnostics (OBD) port.
Rogers stated, “OBD access allows triggering the car to start using other devices. Once the car is tricked into thinking there’s legitimate access, driving is unimpeded.”
Pritchard clarified that criminals likely used an OBD programming tool, which connects to a port usually located under the steering wheel. Mechanics use this port for diagnostics and resetting lights. Pritchard recounted his own experience: “When my Audi was stolen for an armed robbery, they used an OBD tool to program a new key, allowing them to operate the car freely. Something similar likely happened with your Mercedes.”
The experts dismissed the idea of key cloning in my case as overly complex. Similarly, the possibility of a Flipper Zero attack was deemed highly unlikely.
Flipper Zero: An Unlikely Culprit in Mercedes Car Key Theft
Initially, after sharing my experience on social media, some suggested a Flipper Zero attack. One user (@Mayples) mentioned: “Many cars are prone to key fob IR range dupe/focus. They use antenna and a Flipper Zero to replicate the key inside car, unlocks often from antilock-in and then they duplicate the fob into the flipper and drive off.”
Another (@rik_ferguson) suggested: “I’m thinking Flipper Zero or equivalent…Flipper Zero…is capable of unlocking older cars that do not have rolljam or simple relay protection.”
Image depicting a generic car theft scenario, unrelated to Flipper Zero but used to visually represent auto theft concerns.
However, experts interviewed for this article, knowing the full context, deemed Flipper Zero involvement “highly improbable.” Reedman used this exact phrase, and others agreed.
Pritchard dismissed the Flipper Zero theory, referencing the Canadian government’s ban on the device, which they claimed was instrumental in rising auto theft. “As much as the Canadian government would love to blame Flipper Zero, this wasn’t a Flipper attack,” Pritchard stated. While Flipper Zeros are versatile tools capable of wireless network vulnerability checks, access card cloning, and signal transmission, they are not typically associated with sophisticated relay attacks targeting modern Mercedes car key systems.
The Perpetrators: Skill and Accessibility of Car Theft Tools
Having established how my Mercedes was likely stolen through a Mercedes car key relay attack, the question shifts to who is behind these thefts and how they acquire the necessary skills and equipment.
Cluley explained, “The relay attack technique is well-known among car thieves, and instructions are readily available online.”
Rogers emphasized the ease of access to car theft equipment: “Car theft tools are astonishingly easy to obtain. Most car thieves lack deep technical knowledge; they simply use pre-programmed devices to unlock cars.” He clarified that the real expertise lies higher up in the criminal chain, with those involved in R&D and supply of these tools, often connected to other criminal activities like skimming devices.
Pilton added, “The tools aren’t specifically designed for car theft; they’re often for legitimate communication systems and signal extension. However, like crowbars or screwdrivers, criminals repurpose them. The individuals committing the theft may just be using pre-configured tools provided to them.”
Reedman reiterated why he hesitates to call this “hacking”: “It requires minimal skill. They likely watch online videos and purchase relay equipment. It’s trivial.” He argues that true hacking demands a higher level of expertise.
Alarmingly, reports indicate even children as young as 10 are being arrested for car theft, highlighting the simplicity of relay attacks. Direct Line Motor Insurance reported over 1,000 children charged with vehicle theft in three years, confirming the ease with which these attacks can be carried out. Cluley wryly commented, “No doubt they learnt to drive playing Mario Kart and GTA V,” underscoring the low skill barrier.
Mercedes-Benz Response to Keyless Car Theft
With rising automotive theft and keyless entry systems like Mercedes car keys being prime targets, manufacturers face increasing pressure to enhance security. Wright argues, “The automotive industry lags behind most in technological attack protection.”
I contacted Mercedes-Benz for their perspective on keyless vehicle theft and manufacturer accountability. A spokesperson, preferring anonymity, stated, “The security of our organization, products, and services is a top priority in our research and development.”
A stock image of Mercedes-Benz vehicles, used to represent the brand discussed in the article.
The Mercedes spokesperson explained that from mid-2019, the “facelift version of the GLC received a motion sensor in the Mercedes car key. If the key remains still for a period, the KEYLESS GO function deactivates, preventing range extension attacks.” Unfortunately, my 2018 model pre-dated this security upgrade.
“Additionally,” the spokesperson continued, “our Mercedes car keys offer the option to temporarily disable KEYLESS GO, further preventing compromise by range extenders.”
Mercedes is also developing anti-theft measures accessible via the Mercedes me service, including key deactivation through the app if lost or stolen. However, Mercedes declined to comment on why KEYLESS GO deactivation isn’t highlighted to customers at purchase. They also mentioned the GUARD 360° ‘stolen vehicle help’ function, enabling theft reporting via the Mercedes me app and vehicle location assistance in cooperation with authorities.
Shifting Blame and Industry Responsibility
Pritchard contends, “Car manufacturers prioritize ease-of-use over security. Range Rover thefts are so prevalent that JLR now offers its own insurance due to unaffordable premiums from standard insurers.”
Rogers believes car manufacturers lack understanding of the criminal ecosystem and urgency in addressing new theft techniques. “Solutions exist for rapid deployment, but there’s a reluctance to admit the problem. Blame often shifts to victims, suggesting owners should keep keys away from ground floors or block keyless cars with non-keyless vehicles. This is misguided; the negligence lies with manufacturers who are aware of these issues but often inactive.” He also acknowledged manufacturers as victims, emphasizing the need for international law enforcement to target international organized crime groups.
Manufacturers are making some progress. Some now incorporate accelerometers in key fobs to detect motion and activate sleep mode when stationary, thus blocking relay attacks when the Mercedes car key is at rest. Others use ‘time of flight’ technology to precisely measure key distance to the car before authorizing access.
Raising awareness of keyless entry risks at the point of sale is a crucial step. While manufacturers promote convenience, empowering owners with security information for informed decisions is essential.
Cluley adds, “Car manufacturers have known about these risks for years, but solution rollouts are slow, likely due to cost and time implications.”
Pilton suggests shared responsibility, urging collaboration between manufacturers, software developers, and regulatory bodies. “Prevention should include minimum security standards and enabling informed owner decisions.”
The Criminal Justice Bill: A Step Forward?
The UK’s Criminal Justice Bill, introduced in November 2023, aims to criminalize possession of electronic devices used for vehicle theft, including signal jammers and relay attack tools.
Rogers notes a concern within the security research community: “The Bill could chill security research due to potential arrest risks while using these technologies for research to prevent theft and identify vulnerabilities.” The Bill is still under review, offering potential for amendments.
The Appeal of “Dumb Cars”
Criminals naturally target the easiest opportunities. Relay attack car theft is appealing due to its simplicity, lack of forced entry signs, and minimal risk, maximizing resale value for criminals.
Pilton observes, “While traditional key-based systems have weaknesses, keyless entry introduces specific vulnerabilities to methods like relay attacks.”
Cluley concludes, “I’m very glad to have a ‘dumb car’,” highlighting a growing sentiment favoring simpler, less technologically advanced vehicles for security reasons.
My social media post about the theft triggered numerous similar stories, revealing the widespread nature of the problem, low recovery rates, and even rarer prosecutions.
Prosecution Challenges in Mercedes Car Key Theft Cases
Wright laments the “very poor” success rates in finding and prosecuting perpetrators of relay attack thefts. Thieves are often long gone before discovery, tracking systems are disabled, and license plates are quickly changed. Vehicles are often shipped abroad or dismantled in chop shops.
A stock image depicting a car thief, used to visually represent the topic of prosecution challenges.
Rogers mentions successful “stings” targeting overseas car shipments and chop shops but notes these address symptoms, not the root issue of international criminal tool manufacturers.
Pilton recalls investigating cases where cars vanished overnight, making criminal identification exceptionally difficult. “Combating this crime is challenging for law enforcement. While cars are sometimes located, they might be burnt out or already exported. Directly linking suspects to individual thefts is tough without finding the car in the UK. However, organized crime groups often leave ‘breadcrumbs,’ enabling law enforcement to build broader cases.”
A month after my Mercedes theft, neither my car nor the others stolen simultaneously have been recovered. The detective speculated mine might have been used for ATM ram-raiding due to its size. It could be anywhere by now. The “investigation continues,” including forensic analysis and SIM tracking. I hold no hope for recovery, but some for answers and perhaps, prosecution.
Securing Your Mercedes Car Key and Keyless Car
On the night of the theft, my Mercedes car key was in a drawer at the back of my house, naively believing distance was sufficient protection. My cybersecurity expertise failed me personally.
Now, my awareness is heightened. I asked experts for advice on protecting keyless cars, and one word consistently emerged: Faraday.
Cluley advises, “Use a Faraday box or wallet to block signals to and from your Mercedes car keys. Make it a habit to store keys in a Faraday box at home, including spares.”
Reedman recommends testing Faraday effectiveness: “Try unlocking your car from where you store your keys. If it unlocks, a one-way relay attack might work. If not, a one-way relay will likely fail, but two-way attacks are possible. Not all Faraday enclosures are equal; a fully enclosed metal box far from your car is best.”
Traditional advice to store keys away from the front door remains valid.
Rogers suggests disabling keyless ignition if possible, using a mechanical steering lock, and considering an OBDII port lock to deter OBD access.
Pilton stresses social media’s power to raise awareness and encourage preventative action.
Dan Bulman, co-founder of KEYSHIELD, introduced their product claiming “100% protection against key cloning and relay theft.” The KEYSHIELD sleeve wraps around the key fob battery, using motion sensor technology to disable the key’s signal when stationary. Testing on my new car yielded unexpected results; the KEYSHIELD worked too well, preventing even normal unlocking and triggering the alarm. Bulman is investigating potential incompatibility with my car model.
For my new car, I’m adopting a “belt and braces” approach: a Faraday box and a steering wheel lock. Cynicism restored, security prioritized.
Until car manufacturers transparently address keyless car vulnerabilities and educate owners on security options, articles like this aim to empower car owners with knowledge.